
You got this” vs “You got it”. What's the difference - Vocabulary
Price: $ 3.00
5(238)

Qualys Study Reveals How Enterprises Responded to Log4Shell - vulnerability database
MomsRising.org The Future Is What We Do Together
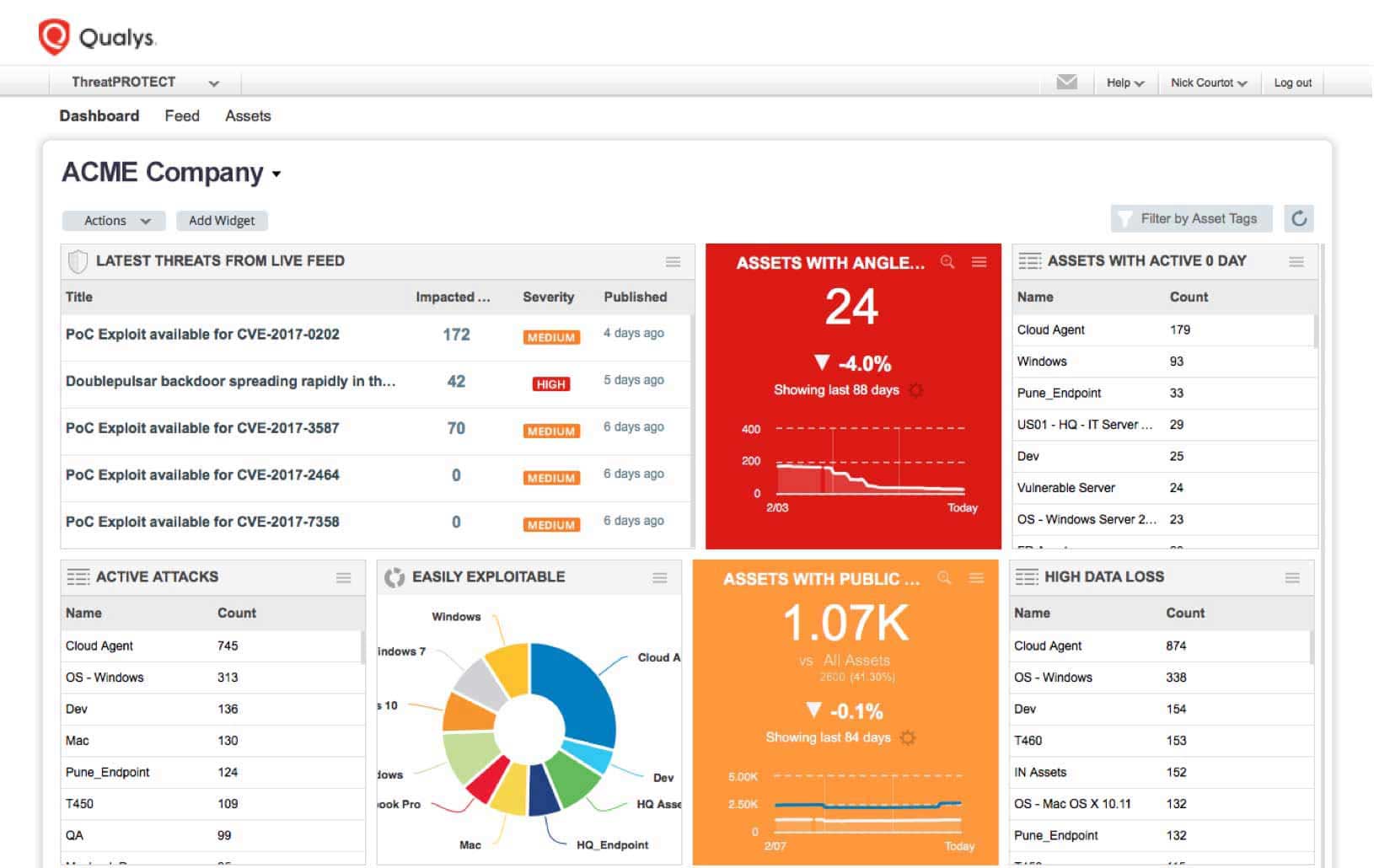
How To Prioritize Vulnerabilities in a Modern IT Environment - vulnerability database

YOUR vs YOU'RE 🤔, What's the difference?
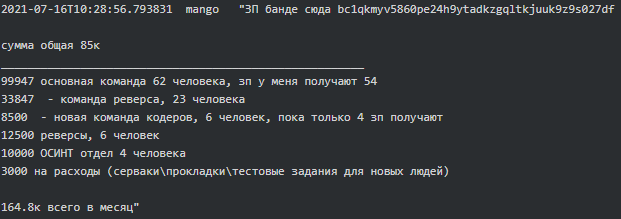
Conti Leaks: Examining the Panama Papers of Ransomware, Tre - vulnerability database
twitminer/Training_Validation_datasets/training.txt at master · vsubhashini/twitminer · GitHub

News & Insights
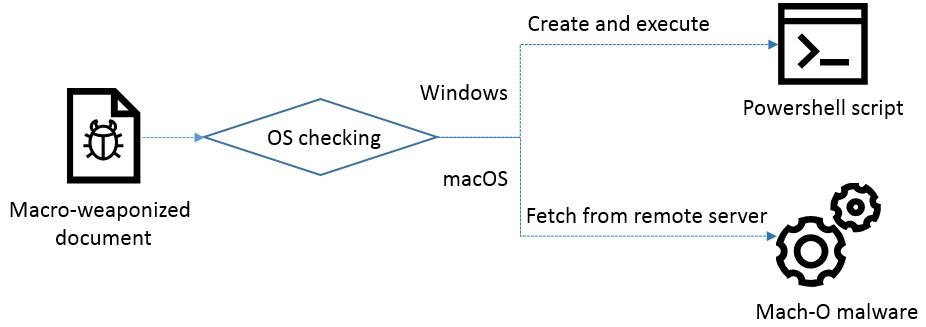
IT threat evolution Q1 2019 - vulnerability database

How fast the use of s02-45 vulnerability to gain server acce - vulnerability database

What's New in InsightVM and Nexpose: Q1 2022 in Review - vulnerability database
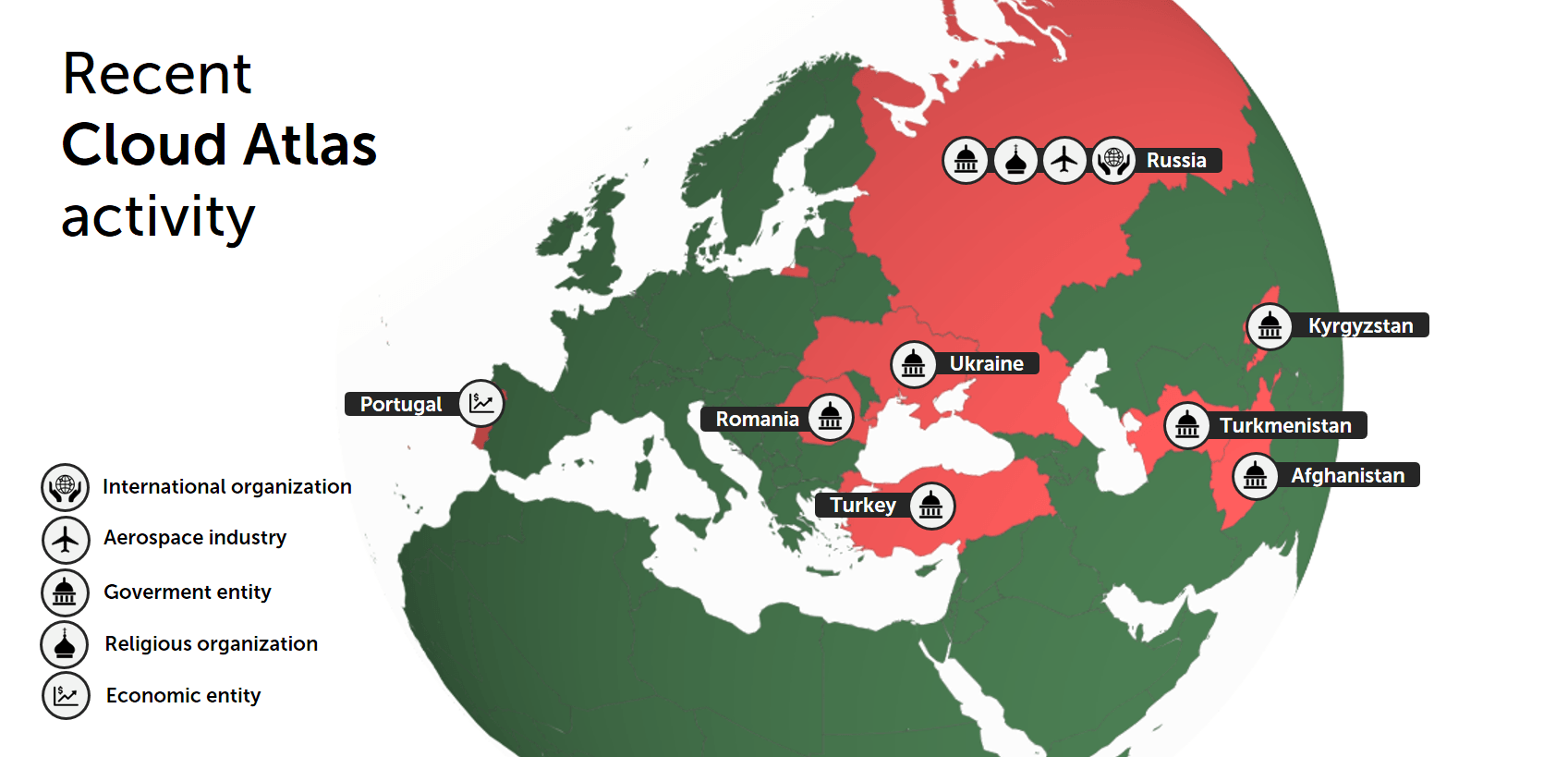
Recent Cloud Atlas activity - vulnerability database
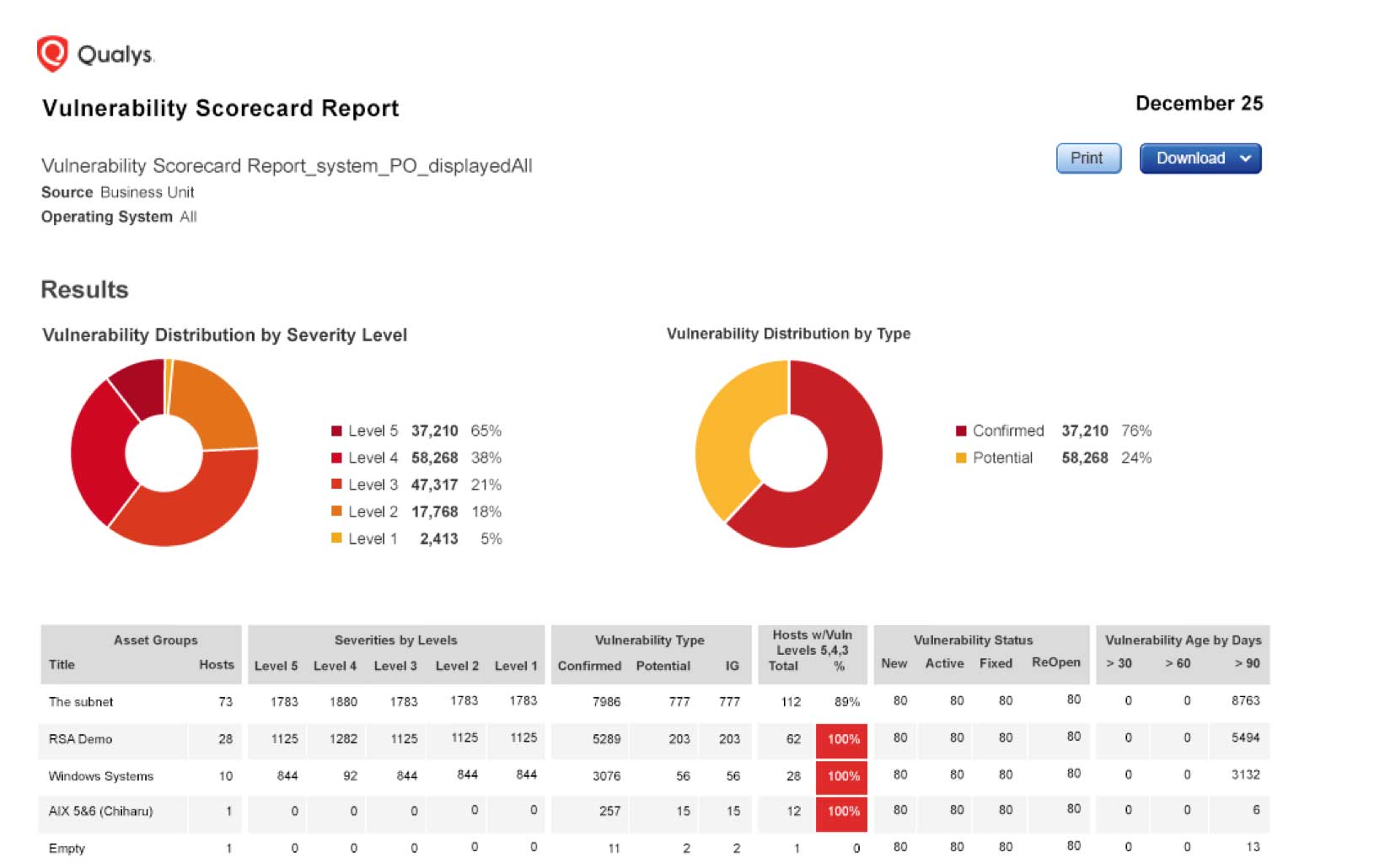
How To Prioritize Vulnerabilities in a Modern IT Environment - vulnerability database



